What is Malware Infection Traffic?
Dridex malware infection traffic is a sophisticated piece of malware that specializes in stealing sensitive information, with a primary focus on banking details. It surfaced in 2014 and has continued to operate as a banking Trojan. Dridex malware commonly propagates through malicious spam emails, also known as malspam, which are distributed in frequent waves, usually two to three times a week. These emails may include infected Microsoft Office attachments or contain links that, when clicked, download malicious files. Below are some examples of Dridex malware distribution methods:
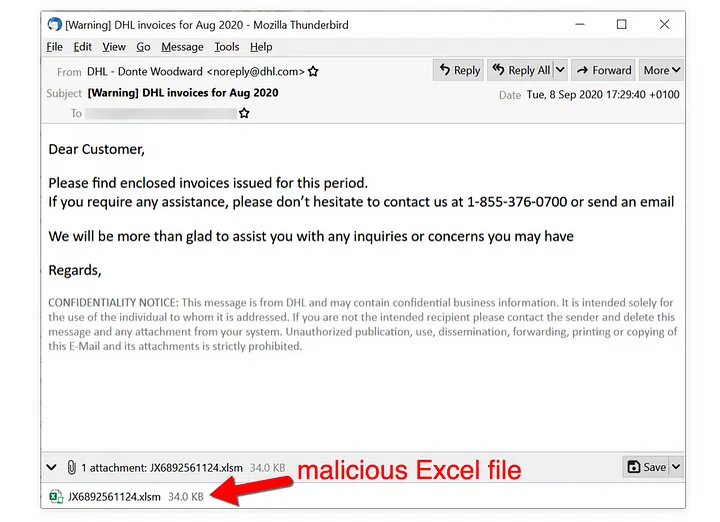
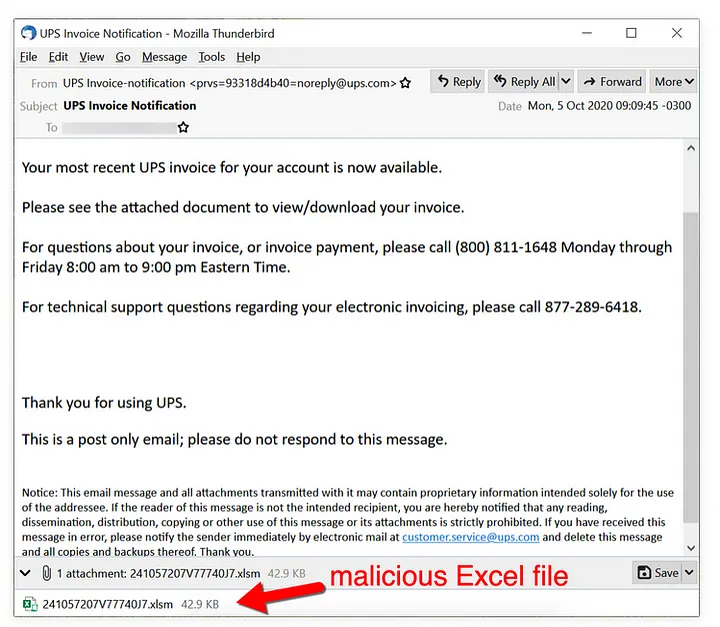
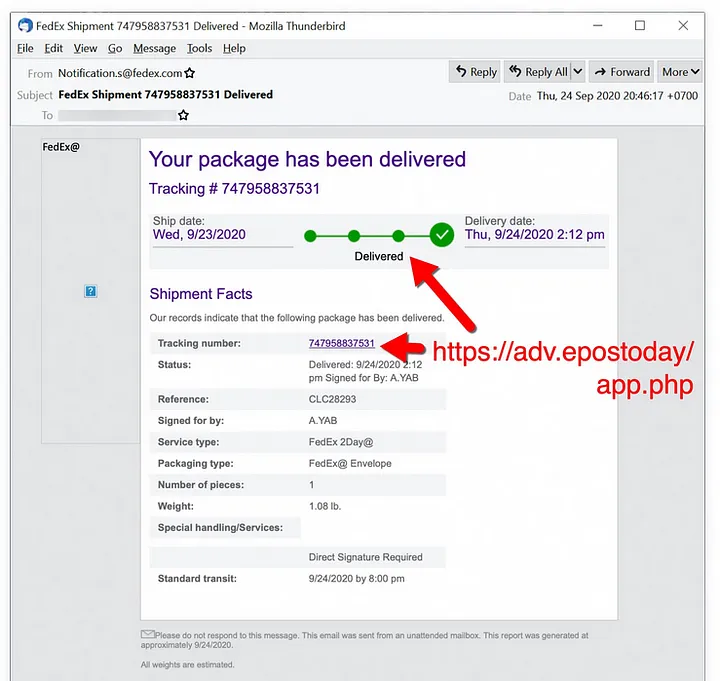
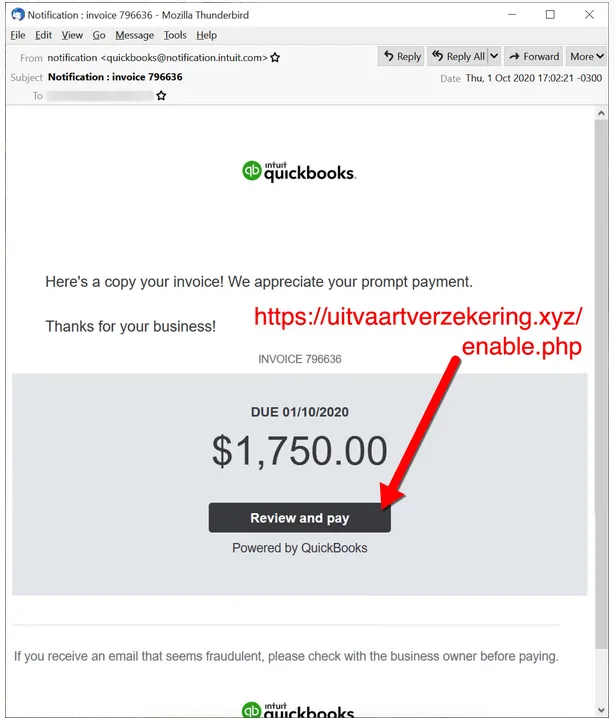
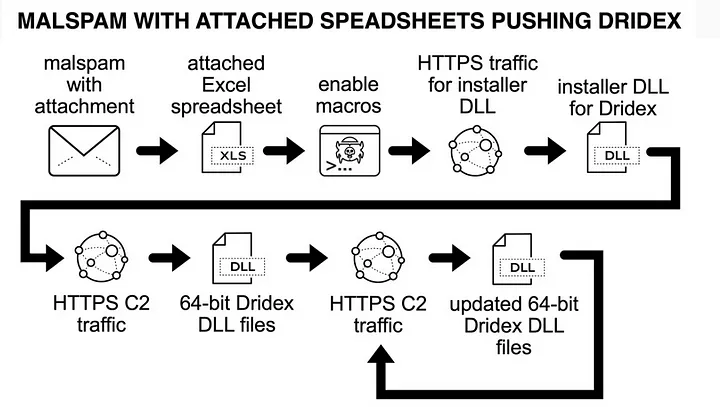
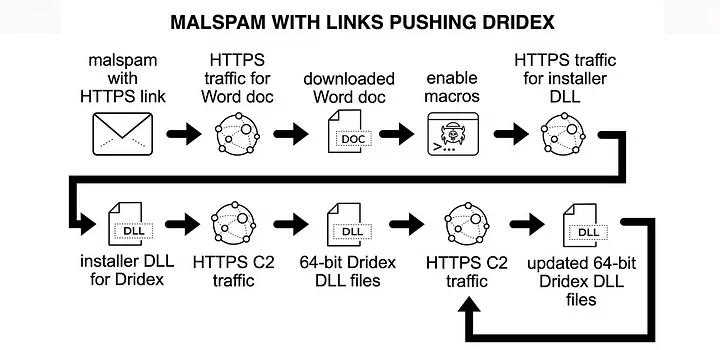
The initial malicious payload could either be a Microsoft Office document with an embedded macro or a Windows executable (EXE) masquerading as a document. Victims need to interact with this initial file, which then downloads a Dridex installer. Sometimes, the initial file is directly the Dridex installer itself. This installer then retrieves 64-bit Dridex DLL files through encrypted command and control (C2) network traffic.
Dridex Infection Chain
The following examples illustrate typical Dridex infection chains observed recently:
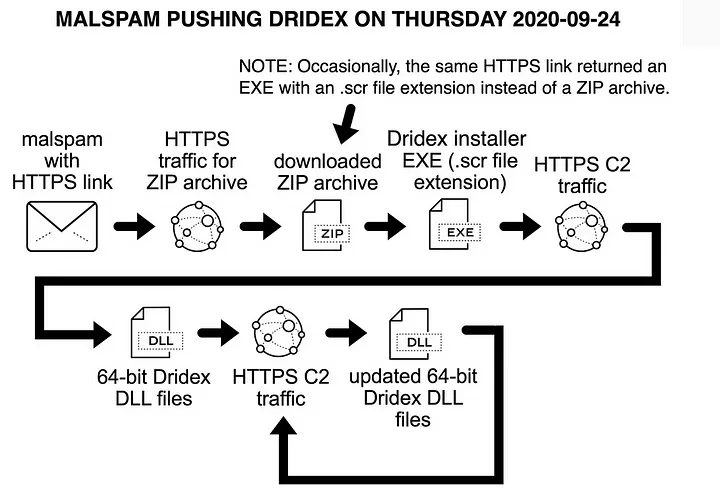
An alternative infection chain observed on September 24, 2020, involved malspam links leading directly to a Windows executable file, rather than an Office document.
How to Analyze Dridex Malware Infection Traffic
Dridex distribution predominantly utilizes HTTPS traffic, which complicates the detection of the initial infected file or the Dridex installer due to encryption. However, the traffic patterns related to Dridex’s C2 activities are distinctive and easier to identify.
Example Analysis: 2020–06–03-Dridex-infection-traffic.pcap
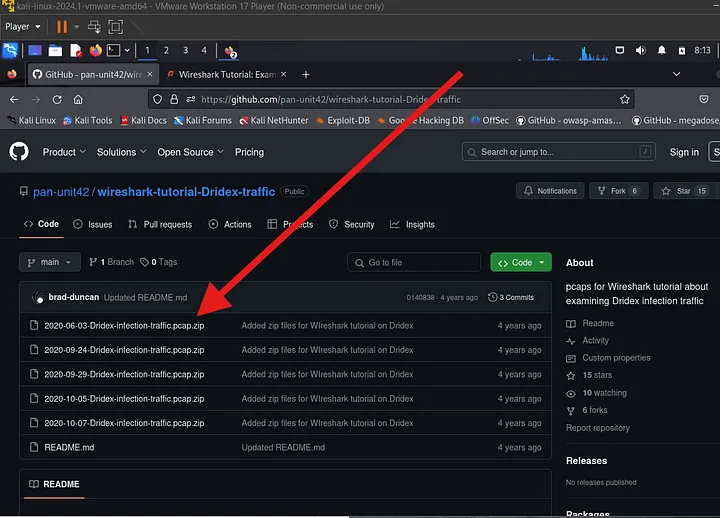
To start analyzing, open the file 2020–06–03-Dridex-infection-traffic.pcap in Wireshark.
Basic filter for Wireshark 3.x:
(http.request or tls.handshake.type eq 1) and !(ssdp)Dridex infection traffic includes two primary components:
- Initial Infection Activity: This occurs when a user clicks on a malicious link or downloads an infected file from an email. This initial activity involves either loading a Dridex installer or the installer being part of the initial file. Since much of this traffic is over HTTPS, tracing specific URLs is challenging, and only domain names are visible.
- Post-Infection C2 Traffic: After the system is infected, C2 traffic over HTTPS communicates directly with IP addresses instead of domain names. This traffic also has unique characteristics in its certificate issuer data, detailed below.
These components together provide insights into the stages and techniques employed by Dridex malware.
Download the .zip file.
Use “infected” as the password.
Open the file with Wireshark to begin analysis.
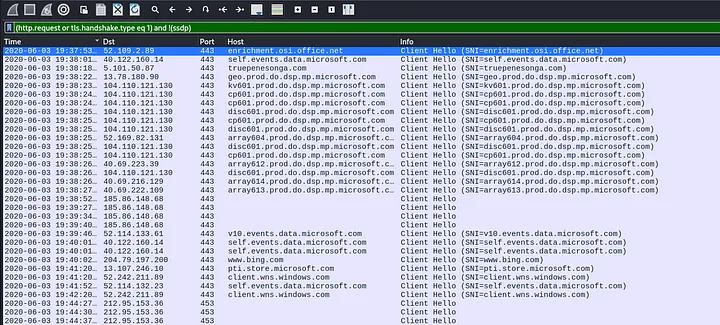
Apply the filter (http.request or tls.handshake.type eq 1) and !(ssdp).
The initial pcap file reveals traffic directed at IP addresses instead of domain names, likely representing Dridex HTTPS C2 traffic:
185.86.148[.]68 over TCP port 443
212.95.153[.]36 over TCP port 453
Basic web filters have identified traffic involving domains typically associated with well-known names like microsoft.com, office.net, or windows.com. Notably, HTTPS traffic to truepenesonga[.]com, appearing early in the pcap at 19:38:18 UTC, is highly likely to be the Dridex installer. A quick online search confirms that truepenesonga[.]com is associated with malware.
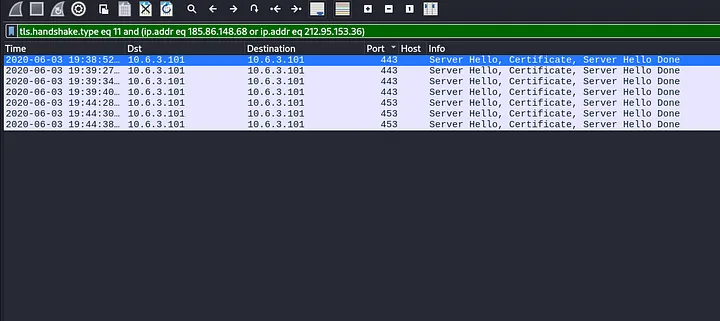
Focus on Dridex C2 traffic post-infection. Use the following Wireshark filter to examine certificate issuer data for HTTPS traffic to these IP addresses:
tls.handshake.type eq 11 and (ip.addr eq 185.86.148.68 or ip.addr eq 212.95.153.36)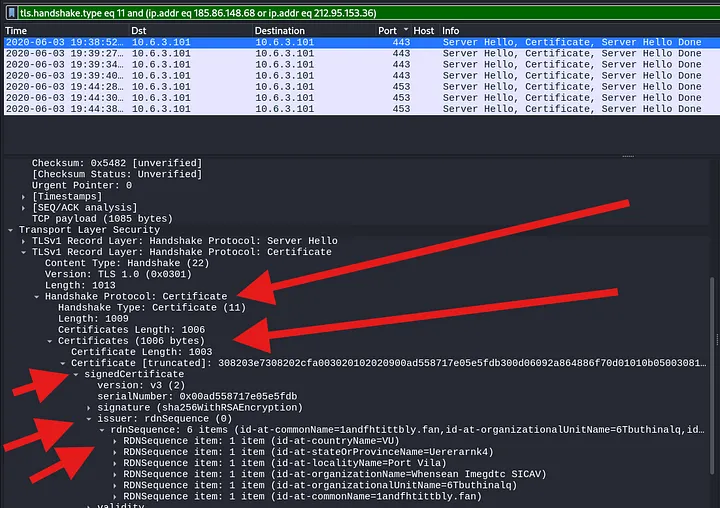
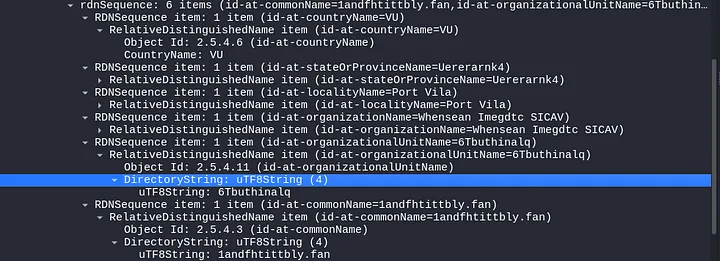
Certificate issuer data for HTTPS traffic to 185.86.148[.]68 includes:
- id-at-countryName=Vu
- id-at-stateOrProvinceName=Uererarnk4
- id-at-localityName=Port Vila
- id-at-organizationName=Whensean Imegdtc SICAV
- id-at-organizationUnitName=6Tbuthinalq
- id-at-commonName=1andfhtittbly.fan
Dridex certificates often contain random strings and numbers, with some consistency in country and city names. For example, “Vu” denotes Vanuatu, and “Port Vila” is its capital.
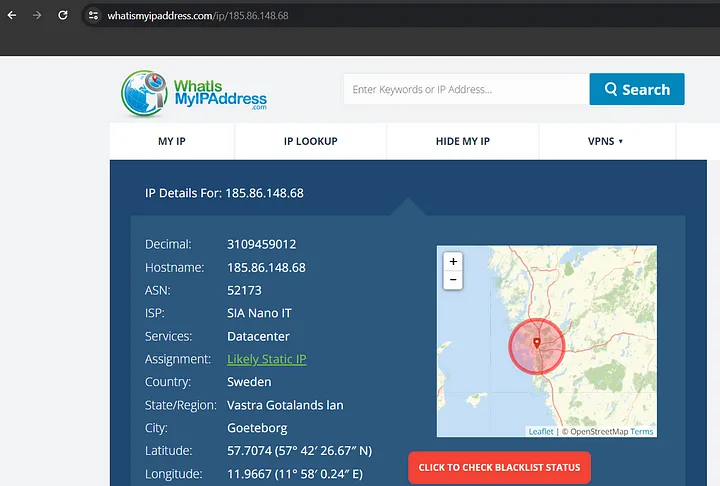
Indicators of Compromise (IOC)
To identify compromised IPs, use lookup services like whatismyip.com. Searching for IP 185.86.148[.]68 yields results shown below.
Conclusion
Dridex malware, known for stealing banking information, spreads through malicious emails and uses encrypted HTTPS traffic, making detection difficult. However, distinct patterns in command-and-control (C2) traffic can be analyzed using Wireshark filters, helping security professionals trace infections and compromised IPs.



