What is ARP Poisoning/Spoofing Attack?
In the realm of computer networking, ARP spoofing—also known as ARP cache poisoning or ARP poison routing—is a method where an attacker sends forged Address Resolution Protocol (ARP) messages onto a local network. The primary objective is to associate the attacker’s MAC address with the IP address of another device, such as the default gateway, leading to the redirection of traffic meant for that IP address to the attacker. So, how to prevent ARP poisoning attacks?
ARP spoofing can facilitate various malicious activities, including data interception, traffic manipulation, or complete network disruption. It is often a precursor to other attacks like denial of service, man-in-the-middle attacks, or session hijacking.
This attack is effective only in networks that utilize ARP and requires the attacker to have access to the same local network segment as the target.
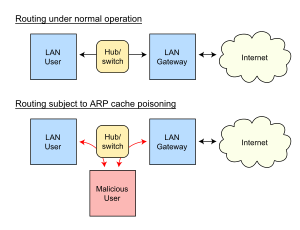
ARP Vulnerabilities
ARP is a commonly used protocol that translates Internet layer addresses (IP addresses) into link layer addresses (MAC addresses). When a datagram is transmitted within a local network, the destination IP address must be converted into a MAC address for data link layer transmission. This is achieved by broadcasting an ARP request, which prompts the destination machine to respond with its MAC address.
However, ARP is a stateless protocol: it caches any ARP replies it receives without verification, and existing ARP cache entries can be overwritten by new replies. This lack of authentication in ARP responses creates a vulnerability that can be exploited through ARP spoofing.
Mechanism of ARP Attack
ARP spoofing exploits the unverified nature of ARP by sending fake ARP messages over the LAN. An attacker can either use a compromised machine within the network or a device directly connected to the target LAN. By masquerading as a legitimate host, the attacker can redirect network traffic intended for a specific IP address to their own machine. The attacker might then monitor, alter, or discard the intercepted data. Alternatively, they can use the attack as a gateway to perform other malicious activities.
How to Prevent ARP Poisoning Attacks
Static ARP Entries
One of the simplest defenses is to use static ARP entries for critical network services. By manually configuring IP-to-MAC address mappings in the ARP cache, a host can avoid generating ARP requests for these addresses. Although this method enhances security against spoofing, it involves significant administrative effort, especially in large networks, due to the need to configure each ARP entry individually.
Detection Software
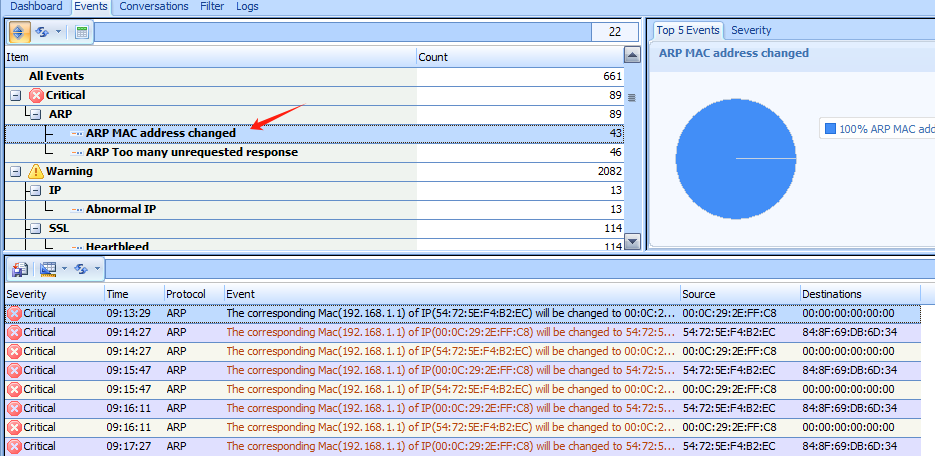
Sax2 IDS is an advanced intrusion detection system designed to monitor and identify abnormal or malicious activities within computer networks and systems. Its built-in detection engine can easily detect ARP spoofing attacks. Please see the diagram below, If ARP spoofing attacks are present in the network, Sax2 NIDS will trigger numerous “ARP MAC address changed” and “ARP Too many unrequested responses” events.
Operating System Security
Operating systems handle ARP caching differently. Linux, for instance, ignores unsolicited ARP replies but updates its cache based on responses to legitimate requests. Solaris updates ARP entries only after a timeout period, while Windows allows configuration of ARP cache behavior through registry settings.
Summary
In conclusion, ARP poisoning or spoofing is a significant security threat that exploits the vulnerabilities in the ARP protocol, allowing attackers to intercept, manipulate, or disrupt network traffic. It requires a multifaceted approach, including implementing static ARP entries, utilizing detection software like Sax2 IDS, and configuring operating system security settings appropriately to prevent ARP poisoning attacks. While each method has its strengths, combining them can provide a more robust defense against ARP-based attacks, ensuring the security and integrity of network communications.


